
Why Technology Alone Can't Secure State Secrets
- Tech alone can’t prevent leaks—88% of breaches come from human error, not flawed tools.
- Pete Hegseth accidentally leaking U.S. war plans shows even top officials are the weak link.
- Security requires a culture of vigilance, not just firewalls and encrypted apps.
Pete Hegseth offered some words of confidence that he immediately aged like curdled milk in a glass of fermented beans. Just days before blundering one of the most hilarious leaks in military intelligence in US history he was bragging about how the US looked like fools under the Biden administration, but now more!
YouTube video linked to the moment (8:47) Hegseth said we looked like fools under the Biden administration
Just 3 days after this video was posted of Pete Hegseth's lofty confidence in the Trump admnistration's merit and skill above the DEI-condoning likes of the Biden admnistration he leaked US military plans to a journalist on a Signal group chat:
 The AtlanticJeffrey Goldberg
The AtlanticJeffrey Goldberg
It's a moment in history that's equally hilarious and terrifying. But there's a lot we can learn from this aside from the amateur professionalism of US leadership. Namely, we can take another critical look at the libertarian value that tech is inherently liberatory. Things like liberation and security cannot be simply outsourced to tech in the absence of human discernment.
Especially given how prevalent user error is. 88% of security breaches are caused by employee user error according to a study titled "Psychology of Human Error" collaborated by Professor Jeff Hancock of Stanford University and Tessian, a security firm. It also revealed that half of employees claimed they're pretty certain they made an error at work that could have led to security breaches. While distraction is a highly rated cause of these lapses in discernment, it's important to note they're not altogether uncommon. And often the weakest link in our digital security is the people interfacing with security tools.
While Hegseth's actions do make him look stupid they're certainly not uncommon. User error is one of the main reasons for security breaches, and there's a lot more federal history for us to laugh about on that subject. For example, there's the 2018 ballistic missile false alarm notification received by Hawaiian residents:
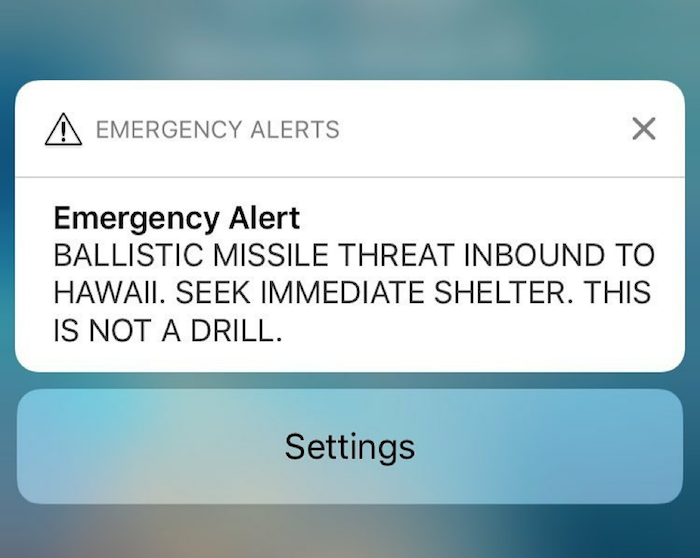
Needless to say, nobody was laughing about this when it happened. After the mass panic was quelled by assurances this notification was sent as a false alarm, Hawaiians called for the negligent employee to be terminated.
Still not as funny as hackers taking over Montana's Emergency Alert System in 2013 when they sent a seemingly official notice to televisions that:
"the bodies of the dead are rising from the dead and attacking the living"
All because Montana's EAS was using factory settings on their security equipment including default passwords. Never forget that the most secure systems in the world are useless without changing the factory defaults.
 Derek GuzmanDerek Guzman
Derek GuzmanDerek Guzman
Since secure tech can't protect us on its own we're going to need to adopt security protocols that make us as users more cohesive with the intention behind cyber security. Not only do we need secure tools, but we need a process for decision-making that uses those tools correctly. Such steps could look like:
- Regular security awareness training: Employees at all levels should receive ongoing education about security risks and best practices.
- Implementing strict access controls: Limiting access to sensitive information on a need-to-know basis can reduce the risk of accidental exposure.
- Fostering a culture of security consciousness: Security should be everyone's responsibility, not just the IT department's.
- Conducting random security audits: Regular checks can help identify potential vulnerabilities before they lead to breaches.
- Using data loss prevention tools and identity management solutions: These technologies can help catch human errors before they result in data breaches.
 Derek GuzmanDerek Guzman
Derek GuzmanDerek Guzman
The US's recent security breach through Pete Hegseth should serve as as reminder that organization from top to bottom can't rely on security tools without human vigilance. Cyber security shouldn't be something that only IT thinks about. It has to be a culture of organizations where every member takes care to avoid negligence around sensitive data. Ultimately the strength of our encryption and the sophistication of our firewalls are no replacement for the diligence and discretion of those we entrust with that information.

